The payment industry is constantly growing where every upgrade plays an important role in developing trust among users by protecting their sensitive data. So, every business that is an active participator needs to meet few security standards that act as armour.
One such globally recognized standard is PCI DSS.
The PCI Security Standards Council came up with a Payment Card Industry Data Security Standard (PCI DSS) framework to protect credit and debit card transactions and card holders’ data from breaches. It is a mandate for every merchant and service provider to abide by this protocol for a smooth customer experience.
How was PCI DSS created?
It all began during the internet boom in the late 1990s, when the initial stage of e-commerce brought in many fraudsters and excitement. When the retailers, merchants, card networks, consumers widely accepted the emerging web-driven transactions, they witnessed a steady increase in credit card fraud and scams. That is when the card networks like American Express, MasterCard, and Visa started to dig deep into the issue to create standards for payment processing systems.
With Visa taking the lead in 2001 “Cardholder Information Security Program” standard was introduced, followed by the other companies implementing their security standards. But it did not meet the expectations of the merchants and POS terminals as they need to comply individually with the company-specific standards. This resulted in great difficulty for merchants as they have to comply with different standards when they are approaching multiple card networks. So, the collaboration of the major card networks such as American Express, Discover, JCB, Mastercard, and Visa birthed PCI DSS version 1.0 in December 2004.
Later in 2006, the Payment Card Industry Security Standards Council (PCI SSC) was formed by a joint venture of MasterCard, American Express, Visa, JCB International, and Discover Financial Services to manage PCI development and alignment of policies to PCI DSS. PCI SSC ensures that the entities are committed to secure credit card data.
PCI DSS is now a globally recognized directive where every merchant who accepts card payments must comply with the latest version, PCI DSS 3.2.1, which was released in May 2018.
Why do merchants need to comply with PCI DSS?
Since there are over multiple card transactions taking place in the market, a safe business environment becomes the prime concern for the merchants to lead a long haul. A business compliant with PCI DSS always earns customers’ trust for their sensitive card information and helps boost the sale and customer confidence. As every business relies on partners, acquirers, or fellow industry mates, being a PCI DSS Compliant helps improve one’s reputation and strategies.
Data breaches, payment card data theft, can be avoided as it is stored securely and monitored on a regular basis. In addition, PCI DSS even helps in improving IT infrastructure efficiency with its compliance levels and requirements.
PCI DSS Compliance levels
There are four levels of PCI DSS Compliance based on the number of annual payment card transactions a business handle.
Level 1: over 6 million TXN
Level 2: 1 to 6 million TXN
Level 3: 20,000 to 1 million TXN
Level 4: fewer than 20,000 TXN
Check out our guide to the PCI DSS Levels and their impact on compliance.
Requirements for PCI DSS Compliance
Every system entity and component associated with Cardholder Data Environment (CDE) must comply with the PCI DSS mandate. It includes requirements for security management, policies, procedures, network architecture, software design, and other critical protective measures.
PCI DSS sets forth 12 requirements for every PCI DSS complaint established by the PCI Security Standards Council:
1. Firewall Configuration
Firewalls are installed and configured to protect card holders’ data from any malware. It helps the prevention systems effectively to defend the hackers from unauthorized access to private data.
2. Password Security
Businesses should not use vendor-supplied defaults for system passwords and other security parameters in their routers, modems, point of sale (POS) systems, and other third-party products. Instead, basic precautions and configurations like changing the password should be followed as the public can easily access the generic passwords and security measures.
3. Protection of Cardholder Data
The stored cardholders’ data must be encrypted with two-fold protection and certain algorithms. Also, the primary account numbers (PAN) must be regularly scanned and monitored to avoid any unencrypted data.
4. Encryption of Transmitted Data
The cardholders’ data should be encrypted when transmitted across open, public networks like payment processors, home offices from local stores, etc. Sharing the account numbers to unknown locations must be avoided.
5. Antivirus Software
All the systems used for interacting, sharing, storing PAN must be protected against malware by regularly using and updating antivirus software or programs. Also, POS providers must employ anti-virus measures and maintain up-to-date antivirus programs to prevent systems from malware.
6. Secure Systems and Applications
To add another layer of protection to the data, the providers must develop and maintain secure systems and applications. These systems and applications that are used as the storage of data for interaction must be updated regularly.
7. Restriction of Access
The cardholders’ data are restricted to access by business need-to-know, and the sensitive data must be accurately documented and updated regularly.
8. Unique Access ID
Individual credentials and ID are assigned to each person with computer access to card holders’ data. Single access ID and password should not be used as it results in more vulnerability and slow response time.
9. Restriction of Physical Access
Card holders’ data must be physically stored in a secured location where any physical access is restricted. Physically written, typed, or digitally stored data must be secured in the room, and in case of any access, it should be added to the access logs.
10. Maintain Access Logs
As mentioned in the previous requirement, all access to network resources and cardholder data must be tracked and monitored in the access logs. This proper record keeping and documentation must be maintained with utmost accuracy as it is related to sensitive data.
11. Testing Security Systems and Processes
Regularly testing/scanning security systems and processes result in less vulnerability as it involves many digital data, software programs/products, physical locations, etc.
12. Document Policies
Document policies that address information security for all personnel must be maintained right from storing to transmitting/using data after POS.
So, with these twelve requirements, PCI DSS comprises six objectives to ensure optimal security for merchants who accept, process, transmit, or store payment card information.
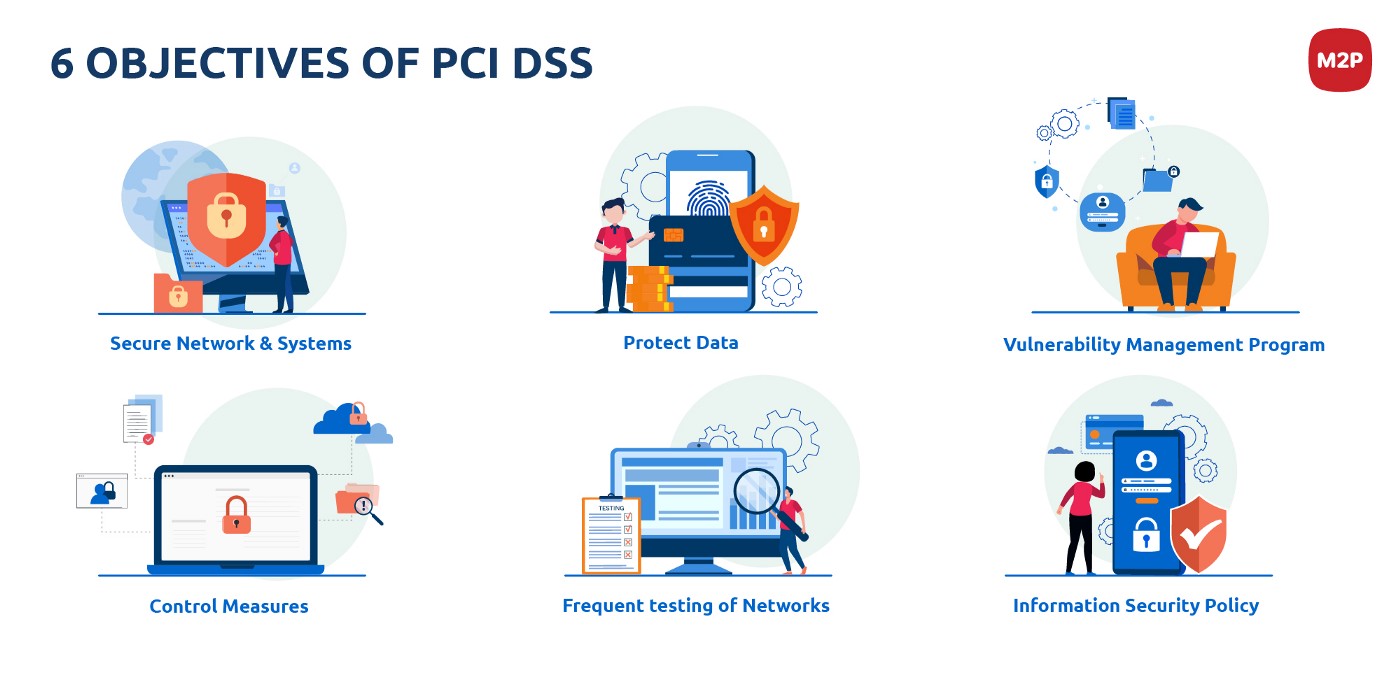
With PCI DSS’s strong objectives and compliance requirements, the security of the payment industry is strengthened. These measures help and encourage data security and facilitate the adoption globally. So, hereby businesses that handle card payments need to be a part of this global payment card data security solution and focus on increasing the intensity to move forward by becoming ‘PCI DSS Complaint.’
Look forward to our upcoming blogs as we uncover PCI SSC’s other standards such as PCI 3 DS, PA DSS, PCI PIN Security, and PCI SSF.
Subscribe to our newsletter and get the latest fintech news, views, and insights, directly to your inbox.
Follow us on LinkedIn and Twitter for insightful fintech tales curated for curious minds like you.




0 Comments