
M2P Fintech
Fintech is evolving every day. That's why you need our newsletter! Get the latest fintech news, views, insights, directly to your inbox every fortnight for FREE!

We live in a world of super apps, where data protection must be prioritized above everything. Safeguarding mobile app information from unauthorized access is imperative to prevent cyber-attacks.
To address security challenges, advanced encryption and decryption mechanisms must be integrated into the Android applications. By implementing robust encryption algorithms such as AES (Advanced Encryption Standard), and incorporating secure key exchange protocols like the Elliptic Curve Diffie-Hellman (ECDH) algorithm, developers can fortify their apps against potential breaches. The ECDH algorithm ensures sensitive data is protected from unauthorized access, enhancing the overall security of applications. This advanced process creates a trusted and secure environment for seamless data transmission.
In this blog, our Code Specialist and Lead Software Development Engineer Janarthanan, will guide you through the intricate world of encryption and decryption logic using AES. With his expertise, you can understand how this cutting-edge technology seamlessly integrates into the Android app, providing a robust shield for sensitive data with utmost ease and efficiency.
To start off, let’s understand cryptographic algorithms.
Cryptographic algorithms (also known as encryption algorithms) are mathematical formulas that define how the encryption and decryption processes are carried out. They define specific steps and operations involved in transforming the data and play a crucial role in the security of encryption systems. The figure below depicts the processes of encryption and decryption, which work together to ensure the confidentiality and integrity of data.

Cryptographic algorithms significantly impact the level of security, performance, and compatibility of the encryption and decryption processes. Now, let's explore AES algorithms, our superhero of data security.
AES acts as a powerful shield that ensures personal data remains confidential and protected. It is commonly used to secure sensitive data such as credit card numbers, passwords, and personal data. It is also used in different applications, including SSL/TLS encryption for web traffic, disk encryption, and email encryption.
Let’s explore the different modes of AES.
When it comes to securing data with Advanced Encryption Standard, different modes can be used. Each mode offers unique characteristics and serves specific purposes in securing sensitive data.

Let’s briefly look at each of the modes before into AES implementation.
Electronic Code Book (ECB) mode independently encrypts fixed-size blocks of plaintext using the same key, which can lead to vulnerabilities. It is not suitable for encrypting large amounts of data or high-security scenarios. Therefore, it is generally not recommended for most encryption purposes.
Cipher Block Chaining (CBC) mode enhances security by incorporating an Initialization Vector (IV). The IV is the same size as the encrypted block and adds an element of randomness to the encryption process. To ensure cryptographic security, each encryption of the same plaintext should produce a different ciphertext.
The Cipher Feedback (CFB) mode of operation can use a block encryptor as a stream cipher. Like other modes, it requires an initialization vector (IV). In CFB mode, the IV is first encrypted and then XORed with the plaintext block to generate the corresponding ciphertext. This process is repeated for each subsequent block, where the previous encryption result is encrypted and XORed with the next plaintext block.
The Output Feedback (OFB) mode of operation allows a block encryptor to function as a stream encryptor without requiring any padding data. In OFB mode, the initialization vector (IV) is encrypted initially, and the resulting encryption is then used to XOR with the plaintext to generate the corresponding ciphertext. This process is repeated for each subsequent block, where the previous encryption results are continuously encrypted and XORed with the next plaintext block. Additionally, the encryption and decryption of the IV cannot be performed in parallel in this mode.
The Counter (CTR) mode of operation uses a counter as the input block for the encryptor. The counter is of the same size as the block being used. In CTR mode, the encryptor generates a keystream by encrypting the counter value using the encryption key. This keystream is then XORed with the corresponding plaintext block to produce the ciphertext. Importantly, each encryption block in CTR mode utilizes the same encryption key, ensuring consistency throughout the encryption process.
The Galois Counter Mode (GCM) is a powerful encryption mode that combines the Counter (CTR) mode with authentication mechanisms. It offers enhanced speed and security thanks to its efficient implementation of table-driven field operations. GCM is primarily used for authenticated encryption, providing confidentiality and authenticity for the encrypted data. It also ensures authenticity for the additional authenticated data (AAD) associated with the encrypted data. It's important to note that the AAD is not encrypted but still benefits from the authentication mechanisms provided by GCM.
When it comes to client-server communication, it is essential to prioritize security. Hackers can easily exploit simple requests during transmission. Let us now look at code implementation in GCM.
When implementing the code, the first step is to Open Android Studio. Once we have Android Studio up and running, the next step is to set up the Gradle build system.
Gradle is an essential component that helps manage dependencies and build configurations for our Android app.
In the Gradle first, the Spongy Castle dependency file is added in the build. Gradle.

Let’s see the steps involved!
The first step is to generate the Key Pair.
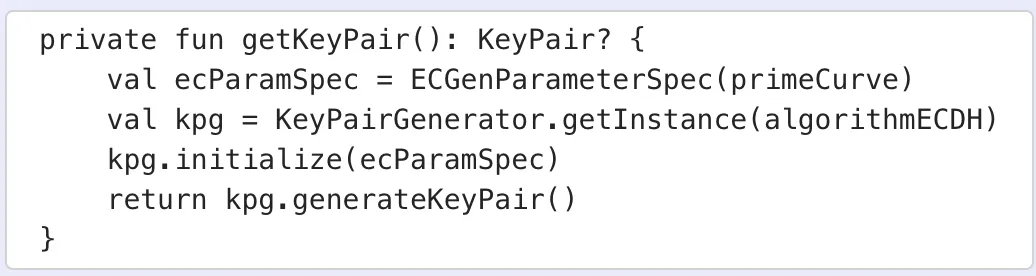
The private key in cryptography is called symmetrical because it involves a single secret key for encryption and decryption. Compared to public-key cryptography, which involves two separate keys (public and private), the symmetrical approach offers faster encryption and decryption processes. To ensure secure communication, both the sender and receiver must possess and use the same private key, making it a crucial component in algorithms like AES 128, AES 192, and AES 256, which enhance the overall robustness of data encryption and decryption.

The public key in cryptography operates on an asymmetrical principle as it involves two distinct keys: private and public keys. Unlike the private key, the public key is used for encryption, while the private key is used for decryption. Due to its inherent nature, public key cryptography tends to be slower than symmetrical private key cryptography. Algorithms like RSA, DSA, and others use the public key for secure encryption processes, ensuring the confidentiality and integrity of data.

To establish secure communication with a web service, it is essential to transmit our public key. Once the web service validates the received public key, it will respond by providing its own public key. This server public key is crucial in generating a secret key for further cryptographic operations.
In secret key encryption, the key used for encryption and decryption remains the same. As a result, ensuring the proper safeguarding and distribution of this key becomes crucial.

Encryption is a crucial process in data security, transforming a normal message (plaintext) into a meaningless form (ciphertext). Its primary objective is to convert plain text into a complex and unreadable format, ensuring that the original message becomes inaccessible to anyone without the decryption key. The output of encryption is a ciphertext, which appears as a series of scrambled characters to unauthorized individuals.

Decryption plays a vital role in data security by reversing the encryption process and converting a meaningless message (ciphertext) back into its original form (plaintext). Its primary objective is to convert the cipher text into plain text. Decryption reverses the encryption process and converts the ciphertext back into plaintext.

The integration of encryption and decryption logic using AES in Android apps has ushered in a new era of data security and confidentiality. By leveraging the power of this advanced cryptographic algorithm, developers can ensure that sensitive information remains protected and inaccessible to unauthorized entities.
Want to know more about enhancing Android app security?
Reach out to us at business@m2pfintech.com.
Subscribe to our newsletter and get the latest fintech news, views, and insights, directly to your inbox.
Follow us on LinkedIn and Twitter for insightful fintech bytes curated for curious minds like you.