
M2P Fintech
Fintech is evolving every day. That's why you need our newsletter! Get the latest fintech news, views, insights, directly to your inbox every fortnight for FREE!

Welcome to our latest blog, where we dive into the critical security technique known as SSL Pinning. This method plays a pivotal role in thwarting eavesdropping attacks on the communication between an app and its server.
SSL Pinning involves a process where, after the initial exchange of encryption keys, the app verifies the validity of the server's certificate. It achieves this by maintaining a list of trusted certificates on the device itself, which are then compared to the server's certificate in real time as the app operates.
If there is a discrepancy, indicating that the server's certificate does not align with the trusted ones, the app promptly halts the connection.
Types of SSL Pinning:
SSL Pinning using Certificate: This method has the drawback that we must update the app each time the pinned certificate expires. However, by anchoring upcoming certificates in the application, this problem may be resolved. We may use the hashed public key, which won't change for subsequent certifications, rather than pinning the entire certificate.
SSL Pinning using server Public key: This method includes attaching the certificate's public key (certificate expiration need not be a concern here).
Mobile applications must retrieve data from the server to display it to consumers. However, private data, such as the user's login and password, is occasionally transmitted between the program and the server. SSL Pinning is mainly used in the prevention of man-in-the-middle attacks.
Man-In-The-Middle Attack
This type of attack allows the attacker to covertly view data passed from the client to the server by using a specialized server called an SSL proxy. It is a tool that encrypts and decrypts data between the client and the server using different keys for each direction. Charles, a proxy server used for testing, is one such example. It works in several phases to intercept and analyze the data between the app and the server. By sitting between the app and the internet, it allows you to examine and modify data in real-time to test the response of the application.
Instead of using the server's key to encrypt data, your app utilizes the public key of the Charles ProxyCertificate. The Charles Certificate is considered valid because the developer can install it on their device.
Charles may connect to the server using its public key after using its private key to decode all the data. Be aware that any developer can read all the data that your app sends over the network.
SSL Pinning using Public Key
Get public certificates using OpenSSL by typing a command in the terminal/console to get the PEM key.
echo "Get HTTP/1.0" | openssl s_client -showcerts -connect
www.MyDomainName.com:443 > myPemCertificateName.pem
Type this command to turn the created PEM key into .der format.
openssl x509 -in "myPemFileName.pem" -inform PEM -out "myDerFileName.der" -outform DER
Use this command to get the public key from the URL in SHA256 format.
openssl s_client -connect www.MyDomainName.com:443 | openssl x509 -pubkey -noout | openssl rsa -pubin -outform der | openssl dgst -sha256 -binary | openssl enc -base64
443 is the safe port for HTTPS. If your website uses a different port, use that number instead of 443.
The result should look like this.
A3r26k+KOMuKJHB5B67cpGqqPhF/GNUyNl2EPJKB65KJUe+hXMn1k=
Generate the Hash Key using this link as well.
Create a variable to store the Public key that we get from the certificate.
static let sslPublicKey =
"A3r26k+KOMuKJHB5B67cpGqqPhF/GNUyN2EPJKB6KJUe+hXMn1k="
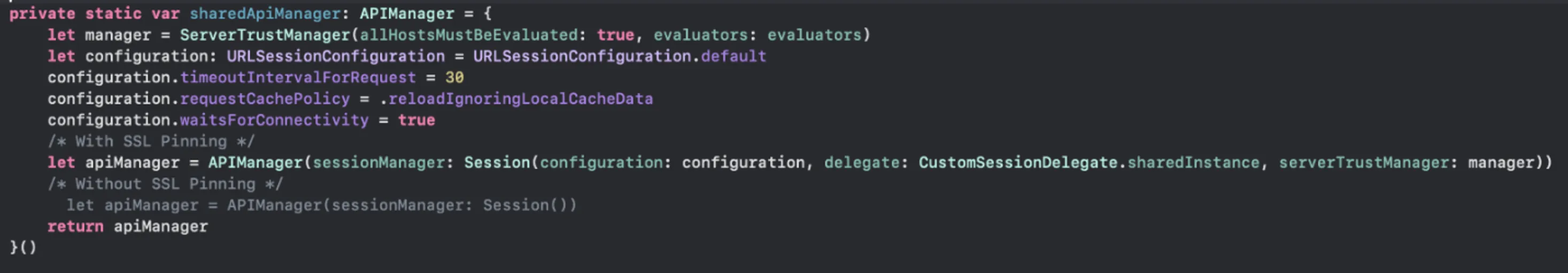
Pinning with Alamofire
Using the regular API can be complicated. Using Alamofire is recommended because it is an external library that offers a simpler way to work with APIs, making your life easier.
The ServerTrustEvaluating protocol is the foundation of everything. It allows us to evaluate server trust in various ways. Alamofire has several trust evaluators. You can read the full documentation here.
Select the ServerTrustEvaluator for each API.

Then create a session with them, and you can customize your configuration.
rsa2048Asn1Header is a list of whole numbers that shows the algorithm and any additional information used with the public key.
This private func sha256(data: Data) -> String function creates a coded hash using the sha256 method for the given data and encodes it in base64.
import CommonCrypto for sha256 algorithm
In SessionDelegate, the URLAuthenticationChallenge method is used to get ServerPublicKeyData
We can perform some actions using this delegate method and match our Public Key with Server Public Key.

Implementing SSL pinning using a public key in iOS enhances security by ensuring that only trusted servers with specific public keys can establish connections. This method mitigates the risks associated with man-in-the-middle attacks and unauthorized access to sensitive data, providing users with a more secure experience.
Stay tuned for more blogs on tech, engineering, and iOS development.
This blog is written by Senthilkumar, SDE 2 – Product Engineering at M2P.